How do I know my school's network has been compromised?
Network hacks have become increasingly frequent in the past few years - especially in schools. The reason being, the less than optimal security...
4 min read
 9ine
:
Updated on May 15, 2025
9ine
:
Updated on May 15, 2025

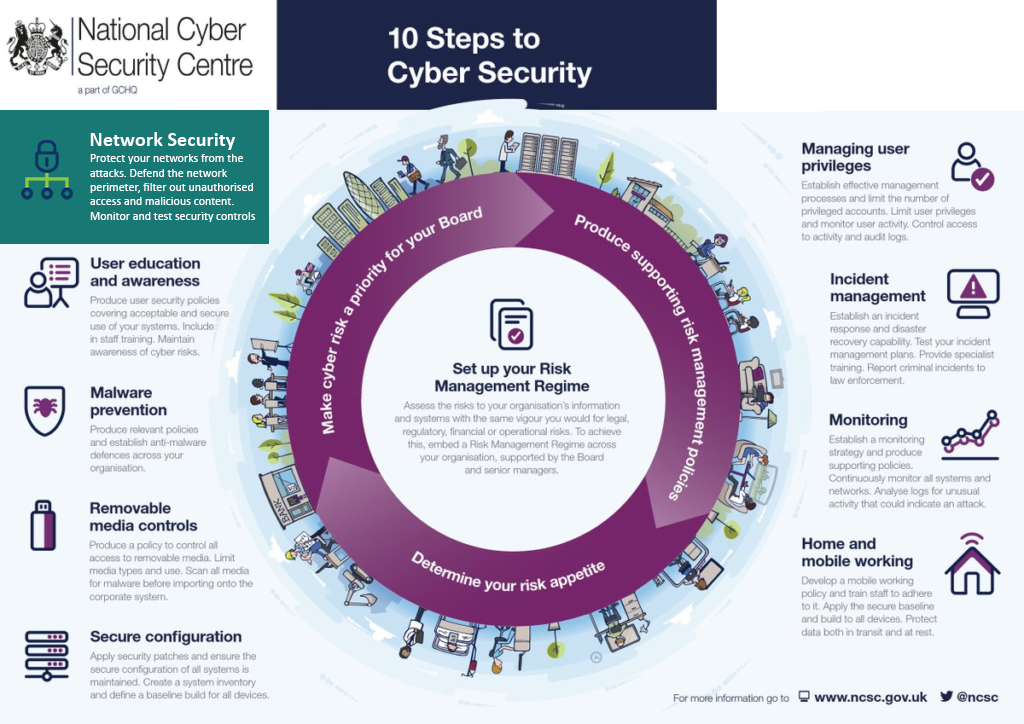
In this blog, the second in the series, we look at Network Security, following the guidance from the UK National Cyber Security Centre (NCSC). We explore how schools can implement technical and organisational changes in order to further protect the confidentiality, integrity, and availability of their information assets. We are building upon each stage of the UK’s National Cyber Security Centre's (NCSC) 10 Steps to Cyber Security and, in turn, providing our independent recommendations, examples and guidance.
In this blog, following the NCSC guidance, we look at Network Security. This topic focuses on the security measures in place around the perimeter of your school's network or on the boundaries between any location where your school's data is held and that of a potential attacker. The physical and logical boundaries between your data, software, and services and the outside world will be explained in the next section.
By following these recommended steps, you will be able to evidence that you are applying and maintaining the appropriate security procedures in order to protect your data, whether it is held on-premises or in the cloud.
Prior to the use of full productivity software and data storage ecosystems like G Suite and Microsoft Office 365, your school’s physical and logical boundary would likely have been the school's firewall. However, the network boundary is now harder to define as your school’s data may be hosted offsite in third-party provider’s data centres (the cloud) and accessed via a wider variety of devices, such as unmanaged "bring your own device" (BYOD), users’ personal devices, as well as your domain-joined devices.
As we have outlined, the network boundaries have moved or evolved. The edge now includes devices that access data while within your school's network and those outside of it, as well as devices that are managed and unmanaged. With the technical and organisational shift as we move more data and services to the cloud, we are becoming increasingly aware that some of these boundaries now sit outside of the school’s direct control. We are relying more and more on the third parties we engage with to apply and maintain the appropriate security measures required to protect our data.
Based on the above, we have listed some of the key areas to reassess and update in order to protect your data from internal or external attack. These include:
The above is not an exhaustive list, but in principle, you need to be looking for any weakness in your school's network that could allow access to school systems and data. Your users’ credentials and accounts are the most common entry point for an attack. Starting with assessing and defining the privileges that are bestowed upon your users when accessing systems and services, and then implementing two-step authentication, is one of your primary lines of defence.
If we look at your users specifically: students, teachers, admin staff, guests, and third-party contractors, ask yourself this:
If we look at user devices specifically: domain-joined devices, bring your own device (BYOD), personal devices, and guest user devices, ask yourself:
The above is a small example of the questions you should be asking yourself in order to determine the appropriate level of access, security and monitoring required to protect your school’s data, whether on-premise or in the cloud.
In order to determine if there are any areas of weakness within the boundaries between both users or devices and the school's data, you need to conduct a technical and operational security assessment. The assessment should look at the effectiveness of the school's systems, services, and users in response to an internal or external technical or organisational attack.
9ine's Cyber Vulnerability Assessments will identify weaknesses in your systems and services that make you susceptible to attack. Identifying areas where systems have not been updated, patched, or misconfigured is key to understanding where and what could allow attackers to exploit known vulnerabilities. Assessing key systems, making use of available security features, and identifying where the application of industry best practises could further enhance your school's security posture.
The output of this exercise will be an assessment, per system, of its operational effectiveness and an associated list of issues and actions that need to be completed to improve your organisation’s security posture. Included within this assessment will be observational assessments and, where possible, examples of what your school needs to change operationally to improve service levels and reduce the probability and impact of a cyber attack.
The Security & Systems Essentials Assessment provides you with a point-in-time evaluation of your school’s vulnerability and response capability to attack. The output of the assessment provides the school with a risk-weighted, prioritised action plan, enabling the school to implement the recommended security controls and mitigation actions in a structured way. This service can be further supplemented by Penetration Tests and Cloud Security Assessments to further validate and ratify the security of the school’s networks and data.
Securing the physical and logical boundaries between your data, software, and services and the outside world is crucial. This is one of the many areas within a multi-layered approach to data security, often referred to as "defense in depth." By following these recommended steps, you will be able to evidence that you are applying and maintaining the appropriate securities in order to protect your data, whether it is held on-premises or in the cloud.
For more information about our Security & Systems Essentials or other security initiatives that we provide:
.png)
Network hacks have become increasingly frequent in the past few years - especially in schools. The reason being, the less than optimal security...

In this fourth blog in the series, we look at Malware Prevention, following the guidance from the UK National Cyber Security Centre (NCSC). We...

Schools are reliant on technology to manage educational resources, student information, and administrative functions. With this dependency comes the...